TODD CALLENDER - BOMBSHELL DISCOVERY DOCUMENTS CONFIRM TARGETING POPULATIONS THROUGH WIRELESS TECH
https://www.bitchute.com/video/W3N9Cr9rmjtb/
I want to also give people the right perspective on all things AI. AI is a novelty, more of a curiosity than anything else people purport it to be, this includes broad statements about where it is going and what it can competently do. My guy feeling is reliance on AI will ultimately bring down the cabal trying to enslave us, because these people appear to be putting a lot of their eggs into an AI-dependant basket.
AI can, and is, being used effectively to skim and scam and generate propaganda that divides and misleads us all. And by combining it with the near bottomless well of information the WEF's stakeholders collect, it is being used with great success to rig entire markets for their benefit, but when it comes to medical applications of the type being proposed all throughout documents and papers like this one, it cannot think its way out of a paper bag, and you need to understand that.
Here are a couple clips that expose just how dumb AI is in that respect:
THE AI REVOLUTION IS ROTTEN TO THE CORE
https://www.youtube.com/watch?v=-MUEXGaxFDA
and this:
https://www.youtube.com/watch?v=DJoGm8c523M
REALLY relevant parallels with copyright law and how computers ruin it, this is where your bio-API hacker exploits will ultimately go.
AI has also proved quite useful to thieves who don't care what encryption protection you think you have:
AI Helps Crack NIST-Recommended Post-Quantum Encryption Algorithm
https://www.securityweek.com/ai-helps-crack-a-nist-recommended-post-quantum-encryption-algorithm/
And the evil cavalcade of bio-weaponry technology continues rolling out in so many ways still. Don't buy any of these fake cover stories about street lamp equipment defects. These lamps are part of this system and they are popping up everywhere by design, not by accident. They serve a specific function in all of this.
PURPLE LIGHTS ALL OVER TEXAS
https://www.bitchute.com/video/HZbFHBViNaQZ/?list=subscriptions
I mentioned one time I had to drive under two of these things on I-95 in a previous article. They FRY you. You can feel it, and they damage your eyesight.
And then there is this:
CELL PHONE TOWERS BLASTING OUT FREQUENCIES ALL OVER THE EAST COAST?
https://www.bitchute.com/video/qNLHrDmxbFTu/
This heat map shows the typical pattern of cell tower traffic ramping up throughout the day and tapering off at night, but when you eventually see it ramping up at night, THAT will be a sign of something very bad. This technology makes people sick deliberately, and the paper I mentioned in the last post plainly discusses by way of multiple measurements how this effect is enhanced by darkness, so that is when they will use it, at night!
I hope this next bit makes you think twice before buying a fancy "smart" anything:
YOUR SMART TV IS WATCHING YOU
https://www.bitchute.com/video/J5JGKvEIU50m/
It's smart. If you buy it, you ain't.
TIMELINE: COVID-19 VACCINES AND MYOCARDITIS
https://www.theepochtimes.com/health/timeline-covid-19-vaccines-and-myocarditis-5317985?utm_source=partner&utm_campaign=ZeroHedge&src_src=partner&src_cmp=ZeroHedge
Is it sinking in yet?
The general public, the masses, generalizing, insist on looking up to their figures of authority for reliable information. They are deeply programmed that the truth must come from above, from someone in a position of power, because they've only assumed that authority would obviously know more than they could. After all, they are just a simple citizen, they say.
And they also wrongly assume that such authorities must always say the truth because they also assume that there is some kind of mechanism behind that would punish them if they didn't do so. And the worst of all assumptions is that those people in power have their best interests in mind.
They don't, and they have never had the best interests of the public in mind. They only have their own, in a heavily narcissistic way, and the interests of the people in power above them.
And the worst part of all this is that many people who are awake and conscious enough to know all this I just said still look up to official authority to make up their minds about whatever is happening near and far from them, also assuming that if they are not well informed, not knowing the latest news will affect their lives somehow.
To me, this is like having a gazelle mentality, always looking around for a dangerous predator. It is not necessary to be watching everything that is going on because if something is really important, you will know it anyway.
It is evident that, from a sheeple perspective, only stupid people—conspiracy theorists—question epistemic truth, as presumably defined by their narrow, authoritarian class. All such stupid people are unintelligent extremists who seek to destroy the social order they disingenuously call liberal democracy.
Anyone who uses the “conspiracy theory” label does so, not because they value the evidence, the facts or the dialectic, but because they will not countenance any challenge to their worldview or any dissent from their claimed authority.
The “conspiracy theory” charge is an authoritarian propaganda construct, intentionally created to censor legitimate, fact-based opinion.
It is time we stand up to the “epistemic authorities” and reject their elitist, authoritarian pretence of intellectual superiority. It is time to insist that all evidence is discussed, that all the facts are established and reported to the public.
It is time to reject the state propagandist’s “conspiracy theory” canard.
This last thing is just a bit of humor that made me chuckle:
A 1953 NEWSPAPER STORY ABOUT THE FUTURE OF THE TELEPHONE - CHECK OUT THAT LAST PARAGRAPH
https://www.bitchute.com/video/nsoa1fHFJVRv/?list=subscriptions
I doubt anyone called this paper back then to complain about woke gay pride. Those were the good old days.
Now, back to the journal paper…
"Field-effect transistors (FETs) are a type of transistors that use an electric field to control the flow of current. FETs consist of three electrodes namely source, drain, and gate. In traditional FETs, voltage is applied to the gate electrode which in turn modulates the conductance between source and drain electrodes. The conductance is reflected as the voltage-current alteration in the output channel. FET based technology is now being utilized for affinity-based electrical sensing using nanomaterials (nanowires, nanotubes, and graphene) as transducer unit [30], [159]. FET transistors can be utilized for biosensing by replacing the gate electrode with a biofunctionalized surface called Biorecognition Unit (BU), for the detection of target molecules in the environment [79]"
So this is where they begin describing how nano-bio devices like biosensors are constructed, which helps you understand how they work, and once you know that you can begin to see where any given component has functional utility, what its specific capabilities and constraining limitations are.
"The BU contains receptors on the surface of the FET channel which binds ligands with intrinsic charges which result in accumulation depletion of carriers in the semiconductor channel, and hence modulation of conductance and current. The addition of BU in conventional FETs for molecular recognition makes them bio-inspired and is therefore called BioFETs. The bioFETs work on the principle of ligand-receptor pairing i.e., binding of a ligand (signaling molecule) to its receptor (receiving molecule) and to produce a response e.g., signal transmission. There a number of ligand-receptor pairs that can be used in modeling BU of bioFETS e.g., antibody-antigen, aptamer-natural ligand, natural receptor/ligand [160] depending upon the target molecule. Semiconductor materials like NW [161], single-walled carbon nanotubes(SWCNT) [162], graphene [163], molybdenum polymers(MoS2) [164] and organic nanomaterials like conducting polymers [165] can be used as transducer channel of bioFETs. Among NW materials, Silicon nanowire (SiNW) has been proven to be the best fit for bioFETs due to their low power consumption, high-speed sampling, high integration density, and high sensitivity [140], [166], [167]."
This is how a biosensor can detect the presence and specific amount of any given substance it is designed to detect and transmit information about. Note that the materials that these biosensors are constructed with are also present in vaccine solutions, so everyone can stop asking the same questions over and over, like "why is that in there?" This is telling you why EVERYTHING in there is in there. It does not matter whether or not anything is inherently harmful, since those responsible for making these vaccines and similar products are not at all concerned with your health. They are all necessary precursors for the ongoing construction of synthetic nanobiological architecture. One of the main objectives of this covert global population experiment is to ascertain upper toxicity limits. Another is to figure out what all can be done to a person if they manage to avoid obvious exposures like vaccinations, but succumb to other basically unavoidable, therefore inevitable exposures.
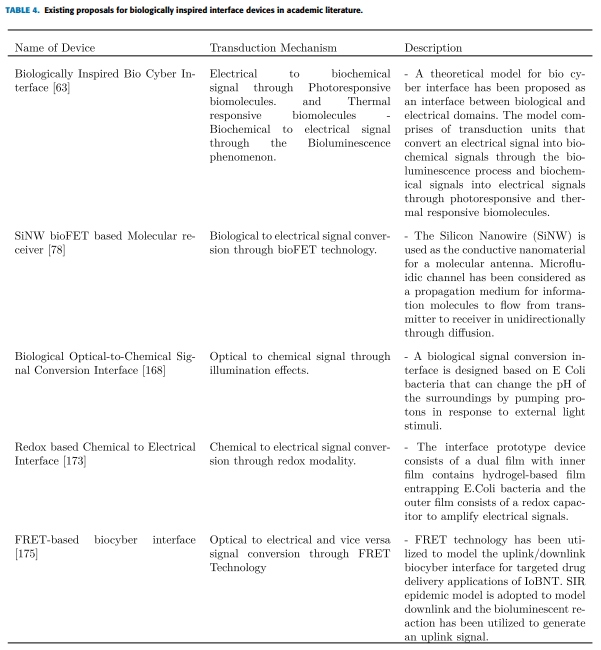
" In this direction, Kuscu and Akan [78] have proposed SiNW bioFET based molecular antenna which receives information molecules as biochemical signals and converts them into equivalent electrical signals. The proposed model employs the theory of ligand-receptor binding and considers microfluidic advection-diffusion channel for the propagation of information ligands. The receiver model consists of three functional units. The Biorecognition Unit (BU) works as the interface for sensing the concentration of ligands. In the Transducer Unit (TU), ligand-receptor regulates the gate potential of the FET through the field effect resultant from their built-in current charges. The output unit shows the current flow as a result of the modulated gate potential. Moreover, an analysis and optimization framework has been presented by providing a closed-form expression for fundamental performance metrics, such as SNR and SEP. The proposed SiNW bioFET is capable of providing efficient in-device, label free and continuous processing of sensed molecules."
In other words, silicon nano-wire biosensors constantly communicate biometric telemetry to whatever collects it.
2) OPTICAL TO CHEMICAL BIOLOGICAL INTERFACE
"Grebenstein et al. [168] proposed a microscale modulator to transduce optical signals into chemical signals. The modulator is realized using synthetically engineered E.Coli bacteria that express protons into the environment upon stimulation from an external light source. Light-emitting diode (LED) of the modulator uses proton pump gloeorhodopsin (GR) to express light. The E.Coli bacteria change the pH level of their surrounding environment as a chemical reaction to an external light source. The proposed testbed achieves higher data rates on the order of 1 bit/min as opposed to previous proposals with data rates of 1 bit/hour."
Transducing optical signals into chemical signals: Again this is the nuts and bolts of electronic drugging. Optical signals are coming from one part of the nanobio system, like a cell full of Luciferase or a similarly enabled nanobot, and this light is interpreted as instructions for some other part, like a drug storage repository.
3) REDOX BASED CHEMICAL TO ELECTRICAL INTERFACE
"New research in biology has recommends the usage of redox as a global signaling modality. Authors in [169] have adopted an approach that is inspired by sonar, which access the redox information through collaborative electrochemical probing. Authors further utilize attuned electrical inputs that are coupled with diffusible redox mediators (electron shuttles) to access redox information in a local environment and generate complex but interpretable electrical output signatures. Redox (Oxidation-Reduction) reaction is also utilized for biochemical-electronic transduction mechanisms in a number of proposals [170]–[174]. A wet lab interface prototype has been proposed recently in [173] for transducing chemical signals into electrical signals by the virtue of redox modality. The interface prototype device consists of a dual film with inner film contains hydrogel-based film entrapping E.Coli bacteria and the outer film consists of a redox capacitor to amplify electrical signals. These cells are engineered as reporters, which respond to the presence of a certain molecule (signaling molecule AI-2) by converting the redox inactive substrate 4-Aminophenyl β-D-galactopyranoside (PAPG) molecules into redox-active p-aminophenol (PAP)."
Just more nuts and bolts ways of talking to your central nervous system.
4) FRET BASED UPLINK/DOWNLINK BIO CYBER INTERFACE FRET
"(Fluorescence Resonance Energy Transfer) mechanism has been adopted by Abd El-Atty et al. [175] to model uplink/downlink bio-cyber interface for the Internet of bio nano things. In FRET-based optical sensing, bio-cyber interface is designed for targeted drug delivery applications of IoBNT. The downlink of bio-cyber interface is designed by adopting spreading principals of SIR (Susceptible, Infected, Recovered) epidemic scheme and decode forward (DF) basis. Three types of nanomachines are used in the downlink model to realize the targeted drug delivery namely nanoreciever, nano transmitter (Infected) and nanorelay(Susceptible) according to SIR epidemic scheme. The recovered nanomachines are ones that have transmitted their exciton to the nano receiver. The uplink is designed by considering two types of nanomachines namely nanosensors and nanoactuators. Uplink signal notifies the medical server about successful drug delivery through bioluminescence reaction."
In other words, a way to rat you out as part of a target group, attack you, and report back to base a successful or unsuccessful exploit.
5) SECURITY CONCERNS IN BIOLOGICALLY INSPIRED BIO CYBER INTERFACE
"Currently the research bio cyber interface security is immature and there is a minimum published literature in this field. Reference [176] have presented the possibility of ML based adversarial attacks for biologically inspired bio cyber interface which are presented below. Details of possible generic attacks on bio cyber interfaces can be found in Section V-B."
Duh. It should be unsurprising that nobody is funding much research on how to protect or defend you, because this is obviously all about creating biologically disruptive technology and NOT about limiting the extent of the destruction.
In the case of bio-luminescent or thermal signaling based bio cyber interface adversaries might launch an attack by manipulating the internet-enabled parameters. By manipulating the parameters, attackers can cause inappropriate amount of drug release, initiate self-annihilation of drug molecules and modify monitoring information provide by bio chemical processes. In redox based bio cyber interfaces, changing the input electrical signal can lead the capacitor charging and unwanted redox activity such as activating/deactivating the redox substrate to affect enzyme production. Bio FETs work on the principals of ligand binding through charging of electrodes. The attacker can launch sentry attack to repel required ligands or black hole attack to attract unwanted ligands to bind to the receptor to affect the current control. The changes in external current control can cause the Bio FET based bio cyber interface to exhibit unwanted behavior.
This describes how an AI can be used to conduct" Kill-Box Ops" that can target and kill you, and it explains how it would accomplish that.
Countermeasures
"The attacks related to biologically inspired bio cyber interfaces can be categorized as ML-adversarial attacks. Possible countermeasures to ML adversarial attacks are [42] Data sanitization: This process refers to pre-processing, validating all the input data, and rejecting the harmful samples. Adversarial training: Inclusion of adversary information in the training samples to recognize attack vector. Defence distillation: Creating secondary ML model with less sensitivity and more general results. Differential privacy: A cryptographic mechanism of adding noise to susceptible features of data. Hormonic encryption. A cryptographic mechanism to perform computations over ciphered data to generate encrypted result."
None of the countermeasures mentioned above are really useful or available techniques for use by people like you and I, but there are others, so we'll get to them, just hang in there.
D. SUMMARY OF BIO CYBER INTERFACE CLASSIFICATION
"It is obvious from the above-mentioned literature that there are a lot of possibilities for designing a bio-cyber interface. The design model of the bio-cyber interface primarily depends on the application scenario. For example, a bio-cyber interface design and components for sensing applications will be different from drug delivery applications. Our take on the choice of bio-cyber interface option goes in the favor of bio-inspired interfaces. The reason being biocompatible in nature and the research in these interfaces in line with the direction of IoBNT. Extensive in-vitro and wet-lab experiments are required to validate the theoretical proposals for the bio-cyber interface."
Now maybe you have an answer to certain questions, like "Why are there still people still pushing vaccines on the public?" or "Why vaccinate the entire world?". It is because, clearly, to a small group of psychotic, impossibly rich globalists, we are all just lab rats. And because they refuse to stop experimenting on us, they have left us with very few alternative ways of dealing with the problems they have created.
There is no other way to put this:
WE HAVE TO HANG THEM ALL BEFORE THEY SUCCEED IN KILLING US.
V. SECURITY IN IoBNT
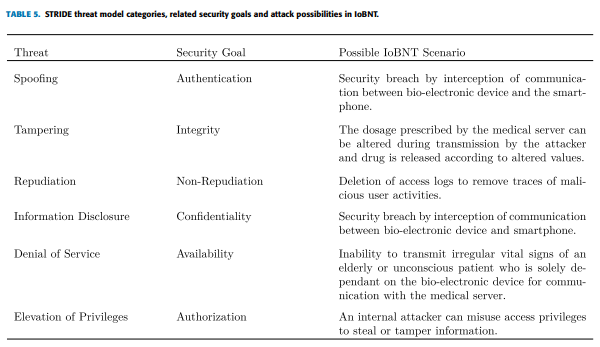
"The advent of skin implanted bio-electronics and the IoBNT paradigm will not only open up a plethora of novel biomedical applications but also its wireless connection capability will enable the adversaries to utilize it malevolently. Connecting the intra-body biological environment with the cyber domain through bio-electronic devices will provide the attackers with an apparent opportunity to devise new terrorist mechanisms to harm the patient remotely. Maliciously accessing the human body through the internet to steal personal information or to create new types of diseases by malevolent programming of bio-electronic devices and intra-body nanonetworks is termed as bio-cyber terrorism [25]. Bio-cyber terrorism can take advantage of wirelessly accessing the human body to launch fatal and life-threatening attacks from a remote site. Therefore security features have to be embedded either in a separate component of the bio-electronic device, which may enlarge the size of the device or might be infeasible in some applications. Another possibility is to delegate security services to external devices in close proximity with sophisticated resources as compared to bioelectronics devices. For example, in a similar field of IMD (Implantable Medical Device), some researchers propose to assign security functionality to an external device like Cloaker or MedMon [177]. Nonetheless, the bio-electronic device must execute a lightweight authentication mechanism at least once to establish a secure connection with external devices. Bio-electronic devices will also be linked to a gateway device (such as a smartphone) to send and receive information from the healthcare practitioner. Because of the technological differences, this section discusses the security needs for nanonetworks and bio-cyber interfaces separately. The security goals, regardless of the underlying technological variations, remain the same. The STRIDE threat approach can be used to model security threats against IoBNT. STRIDE is the acronym for Spoofing, Tampering, Repudiation, and Information Disclosure, Denial of Service and Elevation of privilege. These six categories present a broad classification of threats and can be further divided into other related threats. Each threat category is related to a security goal: Spoofing-Authentication, Tampering-Integrity, Repudiation, Non-Repudiation, Information Disclosure, Confidentiality, Denial of Service- Availability, and Elevation of privileges-Authorization [178], which is presented in Table. 5."
So above you have both the justification for "Hangin Em High" and some thoughts on potential electronic anti bio-hacking gizmos and how such devices might work. However, I would not hold my breath waiting for the same people who are writing this paper to build such devices, or make them available to you.
"Authentication ensures that the identity of each communicating party is established before executing any operation. Moreover, authentication also ensures that the data is coming from the authorized source and unauthorized users cannot access or modify the data. Authentication needs to be done on users as well as a message [29], [179]. Integrity (I): Integrity ensures that the message exchanged between legitimate entities is not tampered or modified by unauthorized entities.
Non- Repudiation (NR):
In the traditional networking paradigm, all the communication transactions are logged to track the network anomalies and gain the attacker’s profile in case the attacker tries to misuse his/her privileges. Nonrepudiation can be violated if the attacker gets access to the logs and delete the records to remove traces.
Confidentiality (C):
Confidentiality ensures that the attacker should not learn the content of the message exchanged between the sender and receiver. The data must only be accessible to authorized personnel upon authentication through some mechanism priory.
Availability (A):
This goal ensures that the services and communication of the device are always available on request.
Authorization (Auth):
Authorization property ensures that only those entities can execute a specific operation that has privileges to order it. Authorization requires that an entity must have been authenticated previously through the regular login (ID, password) procedure to establish the identification."
The various methods described above are pretty self explanatory, so I won't comment on them. They all basically depend on you having access to information you don't have access to, and even if you did you could not be certain it was accurate or complete, so this is a good example of criminal evasive behavior.
i.e. Showing concern for a critical aspect of this kind of R&D while at the same time doing nothing of any significance in that area.
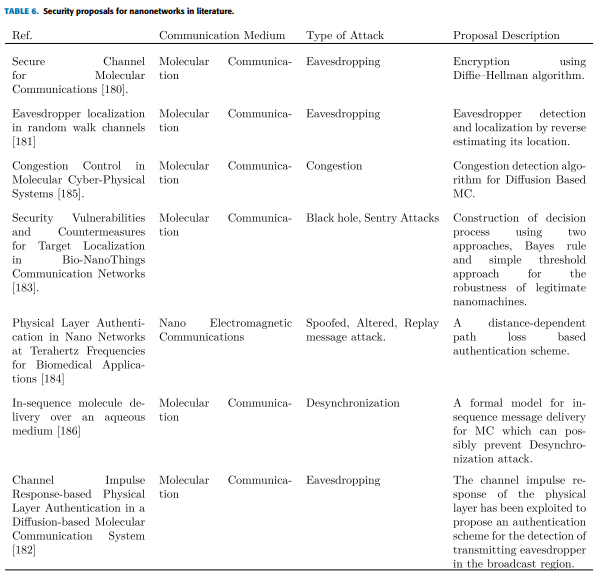
This section presents the possible attacks and existing proposals related to the nanonetworks. A summarization of security proposals for nanonetworks is presented in Table 6.
Everyone is emailing me about the next section and when it will be posted. If I am a little slow completing the dissection and translation of this paper I apologize. Please be patient with me, I promised I would so its all forthcoming. The reason for that is I have come into possession of so much additional and even more informative and incriminating documentation that it has become an intimidating pile.
I am cramming and compiling information at ridiculous pace.
Several people have asked me why I don't do a presentation for MD4CE or some similar presentation on a show like SGT or Stew Peters on all of this. Frankly, it is because right now its hard, even for me, to convey a lot of this verbally or on the fly as I (somewhat embarrassingly) learned during a recent phone call with Albert Benevedes. (The impressive creator behind the WelcometheEagle88 channel on Bitchute.) I found myself struggling at times to answer some of his questions because I was taking the call from the road. Anyway, that is why I probably won't do any media appearances on the Bio-API topic until I feel like I can do a better job of that.
Right now, I need lots of notes to properly answer most common questions, but I do have all of that. What slows me and others down is all the erudite jargon and dual-purpose code speak. There is so much new vocabulary here one needs to become fluent with, and all of that needs to be translated into plain English to make it understandable for lay people.
I have to make people aware of a lot of what is currently in my research pile, because it contains a lot of necessary context for what it otherwise very dry academic literature. I am also trying to compose and collect various visual aids that help break everything down simply.
Like I said before, the learning curve on this stuff is Mount Everest. Nobody is going to get it unless I educate them along the way, so if you feel a bit lost, just hang in there and do the best you can for now. The material I will release very soon, probably before I finish up with this paper, will be very helpful.
-John
HOW TO REVERSE VACCINE INJURIES:
http://estateartistry.com/blog/reversing-vaccine-injuries
CANCER CURE:
http://estateartistry.com/blog/cure-your-cancer-by-christmas
 RSS Feed
RSS Feed