NETWORKING NANO-BIOSENSORS FOR WIRELESS COMMUNICATION IN THE BLOOD
https://phys.org/news/2023-11-networking-nano-biosensors-wireless-communication-blood.amp
UhOh... Problems getting the signal through? Bummer.
LED LIGHTS.
https://www.youtube.com/watch?v=5CyfrRNTKfM
Isn't it interesting that the Biden puppet recently outlawed incandescent bulbs. Hmm, I wonder why. Remember Li-Fi? Optogenetics? Bio-photonics? If not, maybe you should look those terms up and see what they mean. Because these LED bulbs just may be talking to some part of you that you depend on.
THE POLYCRISIS
https://www.zerohedge.com/geopolitical/polycrisis
Look left, now right, now up, now over there… everywhere except where you should be looking.
EU MOVES FORWARD WITH DIGITAL ID DESPITE SECURITY CONCERNS AND POTENTIAL FOR ABUSE
https://www.zerohedge.com/political/eu-moves-forward-digital-id-despite-security-concerns-and-potential-abuse
Think about that picture on the back of every dollar bill, the pyramid with the all seeing eye at the top. Take note of how there is a little gap between the bulk of the pyramid and the cap stone. All of the WEF's key "stakeholders" are up top. Its not as if they do not know their precious vaccines kill people. Its not like the can't see the millions of people that fill the streets of London bitching about this or that.
It isn't that the wheels of governmental bureaucracy turn slowly, or that the voices of millions of dissenters who protest every day, objecting to the global agendas their supposedly elected leaders relentlessly move ahead with cannot be heard.
It's that they are not elected. They are carefully SELECTED… and they are all either well paid or appropriately blackmailed to ensure they turn a blind eye and a deaf ear to all of that.
DID BRICS JUST COVERTLY LAUNCH THEIR CBDC?
https://www.bitchute.com/video/8rZujYVffhFO/
I don't know for sure, but probably.
CBDC won't work unless they can also bulldoze the digital ID through as well. So they way you stop this is to refuse both. The people behind all these agendas are really obvious, even Putin, who is playing the role of a villain and a populist champion at the same time. Listen to Putin and he's defending rights, listen to US political tripe he's the devil. What I would remind this fellow of is: Its all just theater.
Putin is a BRICS big dog, just like China, but everybody has skin in the NWO game, you see them putting on this show basically for you, so you think there are sides to this drama, and to encourage you to take one.
There is only you, "Joe Average" with average wallet size, and the globalists who are actively consolidating everything an obedient sheeple needs to comply with owning nothing and being happy (in front of their screens and video games, all medicated, dying from vaccines, and cheering for whoever is dropping bombs on people they don't know), SO THEY CAN DENY IT WHEN YOU GET OUT OF LINE! That’s what all of this, including the current Gaza conflict, is. It is a "hey, look at the right hand" trick while the left punches you in the nuts.
Don't be a sucker and you won't get sucker punched.
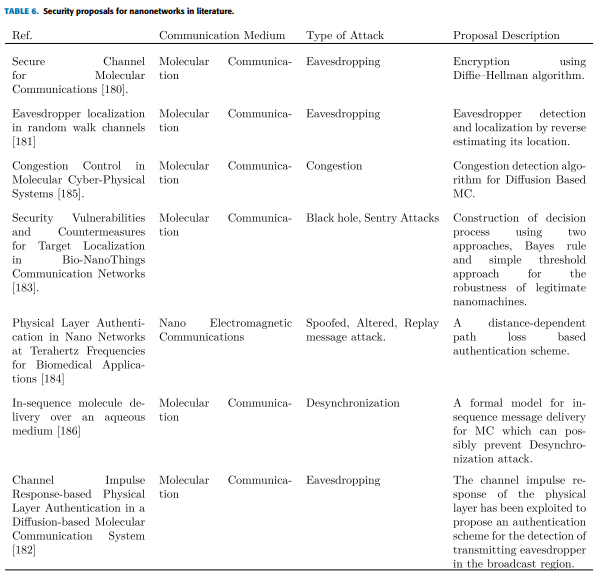
This section presents the possible attacks and existing proposals related to the nanonetworks. A summarization of security proposals for nanonetworks is presented in Table 6.
"Eavesdropping refers to passively listening to the transmission between two nodes. The listened information can be stored and later used maliciously to launch attacks. Eavesdropping in nanonetworks can take place when two legitimate nanomachines are exchanging messenger molecules and a nearby malicious nanomachine intercepts the messenger molecules silently. The passive eavesdropper can be detected in nanonetworks by a mechanism such as stochastic geometry, distance estimation techniques. The active eavesdropper might absorb the messenger molecules in the case where MC is used as a communication medium, this attack might be prevented through secrecy capacity. Other anticipated eavesdropping prevention mechanisms include beamforming, game theory (collation formation games), and artificial noise generation."
Here the discussion is around intercepting either actual molecules or data concerning their presence. In mathematics, stochastic geometry is the study of random spatial patterns, so the discussion is about how available this information is to a potential eavesdropper (hacker) by analyzing things like an eavesdroppers proximity to the information exchange going on. I am not sure what "secrecy capacity" refers to, possibly some sort of encoding that makes the information more difficult to decode. Beamforming refers to methods that are available to limit the possibilities for data interception by focusing the communication much more precisely. Coalition game theory, I believe, is a reference to subset of game theory which involves making deductions about who or where an eavesdropper might be based on his likelihood of belonging to a certain group. Finally, artificial noise generation is just what it sounds like, obfuscating the target of an eavesdropping attempt by muddying up the information the hacker is able to access in some way.
The rest of this section cites a few specific proposals that have been offered about of how these approaches might be used to enhance security, but I don't see anything mentioned below that is new or necessarily bulletproof.
"Several proposals have been demonstrated to detect eavesdropper location and secure the nano communication paradigm from eavesdropping attacks.
Islam et al. [180] proposed a secure channel for Molecular communication. Firstly, a Diffie–Hellman algorithm-based secure key is exchanged between sender nanomachine and receiver nanomachine. Then hardware ciphering is performed using the secret key. As MC is a resource-constrained paradigm, therefore, Exclusive OR (XOR) cipher is used in this work due to its simple implementation and inexpensive computation. Moreover, hardware ciphering used in this work further reduces the associated time, instead of its software counterpart. The results are presented through simulation. In our opinion, the proposed method is simple and computationally less expensive but the overall security is compromised as MC needs more mathematically resilient models for security.
Guo et al. [181] have proposed a mathematical model for eavesdropper detection and localization in a random walk channel. This is the only work in MC that considers the detection of an absorbing malicious receiver in a random walk channel. The authors have chosen transmitter side detection of the eavesdropper because the MC channels are 1-D and receivers cannot affect the transmission and secondly the molecules absorbed at the receiver are quite small that do not aid in detecting eavesdropper presence. Simulation has shown accurate results in detecting the eavesdropper’s presence.
Recently a proposal for physical layer authentication for Diffusion Based Molecular Communication (DbMC) has been proposed in [182]. The channel impulse response of 1-D DbMC has been exploited to detect transmitting eavesdropper in the transmission region."
"Blackhole attack refers to the attack where malicious nodes spread attractant molecules to draw the network traffic towards a different location from the intended target. Blackhole attack is similar to sinkhole attack in WSNs but the sinkhole attack disrupts the routing process while the blackhole attack physically moves legitimate nodes away from the target. When it comes to blackhole attacks in nanonetworks, there are a variety of approaches that can be taken. For example in a scenario of artificial immune system support application, the white blood cells that are responsible for detecting and tackling the infection, can be attracted by malicious nodes to stop them from detecting an infection in the host system."
The place my mind goes to whenever I read something like the section above in red is the converse of any given example. Here the reader is supposed to think in terms of white hat motives, i.e. preventing a hacker from interfering with white blood cells that are trying to attack an infection, but turn that around and you have the opposite scenario; a hacker trying to CAUSE an infection.
Everyplace you look regardless of the literature you choose to read, everything being discussed is framed in terms of patient benefits and physician capabilities, but this tech has been weaponized, so what is really being discussed is how to protect the weaponry, how to make the weapon more effective, more accessible to criminals, etc. You cannot just read it the way it is presented but rather one MUST consider two opposing intents for the use of this technology to see the whole picture.
"Blackhole attack and its countermeasure using two approaches, Bayes rule and simple threshold approach for MC have been proposed in [183]. Blackhole attacks are type of DoS (Denial of Service) attack in which nanomachines can be drawn away for target e-g in case of targeted drug delivery the actuator nodes might not reach the target due to Blackhole attack."
Ask yourself this: Which situation is more likely to require a higher level of security? A situation in which a hacker is trying to deliver a life saving medicine or the situation in which the hacker is trying to poison a target subject? If the situation is one in which insulin delivery or uptake in a diabetic is blocked is blocked, the vulnerability of the diabetic is being leveraged to harm the diabetic. This is how "life saving" capabilities become weapons in the blink of an eye.
3) SENTRY ATTACK
"Sentry attacks are opposite to Blackhole attacks where legitimate nanomachines are impeded away from the target, due to a large number of repellent molecules spread around the target location by malicious nodes. This kind of attack can be fatal in medical applications where instant lifesaving action needs to be taken e-g nanorobots that are designated to prevent bleeding by repairing veins are attacked by a sentry to impede from reaching the target. Sentry attack and its countermeasure using two approaches, Bayes rule, and simple threshold approach have been proposed in [183]. Giaretta et al. [183] have proposed a blackhole attack and sentry attack for MC. The authors have described two scenarios where (L-BNTs) Legitimate Bio-Nano Things are repelled from reaching the targeted site in targeted drug delivery application, thus keeping Bio-Nano Things from performing the normal operation. In the second scenario called black hole attack, M-BNTs (Malicious Bio-Nano Things) are attracted to the targeted site which can lead in a delivery unwanted dosage of medication in the targeted area.
Next, in the proposal, a countermeasure that enables the Bio- NanoThings to make decisions and cooperate in order to overcome blackhole and sentry attacks during target localization is proposed. The mechanisms are based on known cellular decision processes using Bayes’ rule as well as artificially designed genetic circuits that evaluate chemical signal threshold (this will be known as Thresholdbased decision process), which are both lightweight enabling them to be easily implementable on resource constrained Bio- NanoThings. Results show that the proposed countermeasure is effective against the attack, where L-BNTs successfully move towards the target."
What I hear being explained in the section above is how someone can potentially be "medically extorted" by a nanobio-hacker.
"This attack can be launched by malicious nodes by spoofing legitimate nodes identities to become trustable and enter the network. Furthermore, the malicious nodes then send fake messages in the network and alter the data. In the case of nanonetworks, consider an exemplary communication scenario where a legitimate node ‘Alice’ is transmitting messages to receiver ‘Bob’. Attack can be launched by an intruder ‘‘Eave’’ impersonates to be Alice and tries to control Bob by sending malicious commands.
A distance-dependent path loss based authentication scheme for nanonetworks using the terahertz band has been proposed in [184] for spoofing attacks. Rahman et al. [184] have proposed an authentication scheme for terahertz band EMbased nanonetworks. This work exploits physical layer attribute i.e., distance-dependent path loss for authentication at nano receiver. Moreover, an algorithmic solution has been proposed for the authentication scheme. Experimentation verification of authentication scheme via tera hertz time-domain spectroscopy setup at QMUL, UK."
This is where I begin to get very concerned, because this is the type of exploit I believe is being used to electronically torture those people known as "targeted individuals". I have interviewed some of these folks, and the things they report happening to them can be truly shocking.
What I can tell you authoritatively about this is this type of exploit is it includes making of use of a persons own electroencephalogram patterns to harass them. It has become known that anything your body and brain perceive is the result of electrical signals generated by your central nervous system. These signals can be reduced to EEG patterns that can now be recorded and played back.
What has also become known is the fact that your patterns are unique to you. One cannot transmit a recording of someone else's EEG patterns to you and cause any reliable effect with that procedure, but if your own EEG patterns are recorded, something that is possible with all these embedded biosensors and associated medical data cloud storage, and then replayed by re-transmitting them back to you, something that is also possible with the same nanotech, then you will re-experience the recorded event JUST AS IF IT IS HAPPENING TO YOU ALL OVER AGAIN! The target of such an attack is physically unable to distinguish between actual stimulus and simulated stimulus.
Now this makes for some really frightening scenarios. If, for example, you are selected as a target, a handler, (which does not have to be a human being, many times this is accomplished with an AI program), will monitor you over a period of time. During that time actual people may present situations, provide stimulus, or place you in certain situations you must react to, to ensure they are recording your EEG readings in various emotional states, under different levels of stress, whatever it is they want to use later. If these recordings are then re-transmitted back to you surreptitiously, they can literally drive you crazy with them.
They can force a person to re-experience whatever experience they have recorded as if it was happening all over again, which is what many targeted individuals report. Hallucinations, sounds… anything. Instant fight or flight reactions can be induced over nothing and at any time. So you can see how sinister a threat this can be if we are using this nanotech for medical monitoring on a widespread basis, and that is exactly what they are doing.
File those recordings away with a unique identifier, in this case it is that Bluetooth ID the vaccinated all have, and some spook has an instantly accessible control file on you that allows real control over you.
This is the capability they have been cultivating all this time and selling to everyone in the form of various benefits, like making the blind see, the lame walk, direct neuro-prosthesis control, early detection of diseases, and so on.
A distinct subset of these patterns also run your autonomic nervous system, so this would include the electrical signals that cause your heart to beat regularly or cause your breathing to be automatic. All those bodily functions that you don't have to consciously think about are included as part of your autonomic nervous system. Give a bad actor control over these functions and a bio-hacker can murder you and make it look like an accident. They can cause a stroke, give you a disease, or induce some sort of mental psychosis that will drive you, unaware, into the psychiatric profession where you can be institutionalized.
Imagine the level of influence one could have over a head of state, were he to become compromised in this way through what he thought was a simple vaccination. And these are exactly the sort of advantages pitched by people like James Giordano when he lectures on deploying weaponized IoBNT in intelligence applications.
Think this is not being used today? Think again. Giordano comes right out and admits it, without the slightest hesitation, even openly stating that the kind of manipulations made possible by synthetic biology is currently actively deployed and being used everywhere.
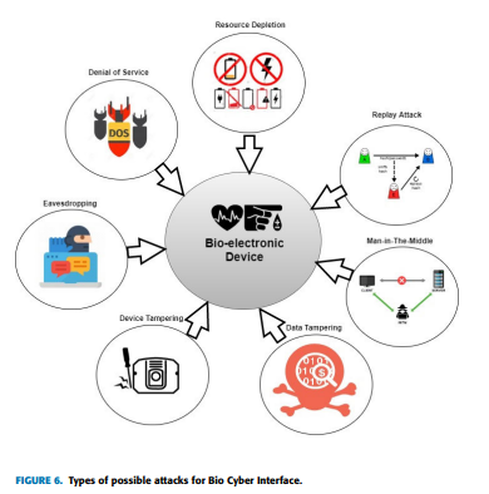
B. ATTACK TYPES IN BIO CYBER INTERFACE
"To ensure an end-to-end protection of IoBNT applications, the security of these bio-electronic devices is a prerequisite. In order to pursue a preliminary investigation for types of attacks that are possible in bio-electronic devices, the attack vectors are explored in related fields like WBAN. (Wireless Body Area Network) [28], IMD (Implantable Medical Devices) [178] and Wireless sensor networks [187]. This investigation has helped us to individuate attacks that are likely to occur in bio-electronic devices. The major objective of a bio-electronic device in the IoBNT healthcare application is to enable two-way communication between intra-body nanonetworks and healthcare provider. The communication mode is divided into two categories: inbound and outbound, making it easier to recognize and categorize attacks. Figure 6 presents possible attack types in case of bio cyber interface."
Are you paying attention? I hope so. They are talking about the abuse of wireless body sensor networks, the whole focus of another paper I mentioned in this post: http://estateartistry.com/blog/now-do-you-believe-me
"Eavesdropping is a passive attack that enables the attacker to covertly gain access to confidential information. The bio-electronic device might possess critical information like patient identification information, clinical history, disease detail, treatment detail, patient location, and battery status, etc. This confidential information can be exploited not only to breach a patient’s privacy, but also to launch other types of active attacks. Eavesdropping can be realized during the communication of bio-electronic devices with biological nanonetworks and during communication with the gateway devices.
Countermeasures:
Traditional networking paradigms employ encryption schemes like RSA and DES, to prevent against eavesdropping attacks. These encryption schemes are effective for the prevention of eavesdropping attacks, but these are computationally expensive and must be adopted after analyzing the resources of bio-electronic devices [188]. Lightweight encryption schemes like Elliptic Curve cryptography has been proven to be effective for resource-constrained devices [189], also a review on other lightweight encryption schemes has been presented in [190]"
Do you hear in this last paragraph how someone is already complaining about how difficult it is to protect this system with traditional encryption?
2) REPLAY ATTACK
"This type of attack can be launched after a successful eavesdropping attempt. The eavesdropped authentication sequence of the legitimate devices can be replayed to get illegitimate access into the communication channel. Moreover, an attacker can copy previously sent commands from legitimate users to replay the message again which in the case of bio-electronic can have a number of consequences like drug release multiple times which harm patient’s health, unnecessary and repeated queries for patients physiological values to engage and deplete the resources, etc.
Countermeasures:
Authentication schemes, Intrusion detection, delegate authentication to external devices. (See Section VI)."
3) MAN-IN-THE-MIDDLE (MITM) ATTACK
"A MITM attack is projected through illegitimate devices when they become part of communication between legitimate transmitting devices, and legitimate devices are spoofed to believe that they are communicating with the authorized device. In the case of bio-electronic devices, the attacker must be in the vicinity of the patient to launch the MITM attack. From the communication perspective, the MITM attack can be achieved by replaying the legitimate authentication sequence to get access to the communication channel. MITM is the type of an active eavesdropping attack where the attacker not only listens to the communication but also alters the data and communication sequence.
Countermeasures:
Traditionally MITM is prevented using encryption schemes. A lightweight scheme to prevent implantable medical devices from MITM attacks has been proposed that utilize chaotic generators for randomness and a signature algorithm to prevent third-party interference [191]."
Unfortunately, there is currently no encryption scheme that cannot be broken, which means there is no viable protection against this kind of exploit.
4) RESOURCE DEPLETION (RD)
"Bio-electronic devices are essentially capable of performing in-situ [77] operations and for this purpose they contain built-in processing unit, memory unit, and power unit. However, these units are only able to perform trivial tasks due to resource limitation in terms of space, power consumption and computation complexity, which comes with their minute size. The attacker can cause resource depletion by sending multiple authentication messages with the wrong credentials to occupy the processor. Each authentication request is processed which exploits the memory to create access logs and drains the battery. Moreover, bogus communication packets sent by MITM can utilize and drain the resources.
This sounds to me less like a hacker exploit and more like a way around limited nano resource limitations.
Countermeasures:
Access control mechanisms, Anomaly detection system, user notification, and use of rechargeable batteries. Moreover, mitigation from resource depletion attacks can be achieved by using passive wireless communication media like RF signals and the use of novel energy preserving techniques like ZPD (ZeroPower Defence) [192]."
Again, I hear this paper discussing how to maintain control by overcoming the limitations of an underpowered nanobio network installation. A LOT of what is covered in papers like this can be read two entirely different ways depending on what one considers "a potential problem" to be. You must always think, "problem for whom?"
"Injection attack can be performed by the illegitimate users in three ways, insertion, alteration and replication [135]. In insertion attack, hacker generates new seemingly legitimate data packet into the communication channel. In alteration attack, hacker captures the data packet from communication link, tampers with the values of dosage commands from the inbound channel and alter the values of bodily parameters in the outbound channel. In replication attack, attacker re-sends previously executed commands into the system. Insecure communication between bio-electronic and gateway devices can result in an injection attack. This attack can have fatal consequences on the patient. For example in a scenario where a diabetic patient is fully dependent on wirelessly controlled insulin and glucose monitoring pump [73], the alteration in dosage values received from health care provider can result in hazardous consequences like underdose can cause hyperglycemia and overdose can result in hypoglycemia both of which can be fatal [193].
Countermeasures:
Careful mitigation strategies are needed to be designed which include authentication protocols [194], access control mechanisms [178] Intrusion Detection, Input validation, and Authorization techniques."
In other words… they don't have any countermeasures for this yet.
6) DEVICE TAMPERING
"This attack is majorly launched in the bio-electronic devices by local attackers, due to low transmission range of bio-electronic devices. The device can be reprogrammed or physically replaced to perform the malicious tasks that are not intended by the device in the first place. This attack can also be launched by accessing the device remotely by sending fake firmware update and device upgrade message that alter the software configuration of the device to perform maliciously [195]. This attacker can alter the original treatment prescribed by the healthcare provider and replace it with false treatment which can cause life threatening consequences.
Countermeasures:
Tamper proofing and self destruction, device hardening, and Physically unclonable Function (PUF)."
Yeah, keep talking. Not buying it.
"Denial of service attack causes disruption and blockage of information flow between legitimate communicating parties. An attacker tries to suspend services of the bio-electronic device to make it unavailable for communication and processing. DoS can be launched in the form of any of the above-mentioned attacks. The DoS attacks such as battery drainage, sleep deprivation and outage attacks can be performed by hackers after getting access to the devices. As the power source of these devices is limited and attackers can send an unlimited number of messages, causing the battery to drain. In outage attacks the device can be made unavailable by stopping it from carrying its essential functions, behaving abnormally or premature shutdown. These types of attacks can pose serious consequences for the patients [135]. Moreover, the hacker can intentionally drop the forwarded packets, making the recipient deprived of requested data.
In other words, say a person is compromised such that medically they need something regularly to survive and that thing is delivered electronically. All ya gotta do is interfere with the delivery of whatever that life saving thing is, and they go poof.
Countermeasures:
Intrusion Detection."
(Go Onnn… How? Oh sorry, you got nothin)
8) MALWARE ATTACKS
"Malware attack is another type of network attack that is common in IoT based applications. Malware attack is used to remote control a distant device maliciously, steal sensitive information from a device and use it to launch further malware attacks. A system infected with malware attack may start running certain programs automatically like sending messages, re-configuring internal software and turning of anti virus. In case of IoBNT application an infected bio cyber interface might start dispensing inappropriate amount of drugs, thus causing harm to the patient. Some of the popular malware attacks that are still active in IoT environments are Mirai, Echobot, Reaper, Emotet, Gamut and Nucer [196]. There different types of malware attacks, but malware attacks specific to IoBNT applications can be botnets, rootkit, ransomware, and keylogger attack.
Botnets: In this type of attack, attacker gains access to a number interconnected devices by launching malware and further control them to steal information, launch DDoS (Destributed Denial of Service) attack to launch unplanned system downtime and even sell network access to other cyber criminals.
Let's get real for just one moment, pull back from the microscope and recall some of the more "Macro" sized crimes we all saw recently. Could this botnet model also be used to describe the act of capturing a whole bunch of government regulatory agencies to enable a bunch of criminals to deny you of your right to bodily autonomy?
Ransomeware: The attacker gets hold of the device by encrypting user’s data and locks the device, thus, restricting access of the owner to the device. The attacker than demands for some ransom amount by displaying messages on the device screen.
And if the device in this example is your body…?
Keylogger: It is a malicious piece of code that records the keystrokes of user to gain access to ID and passwords. This attack is dangerous than brute force attacks and strong passwords does not provide protection against this malware.
Kind of sounds like what happened when you were told you were getting a life saving vaccine when what was really happening is you were injected with a whole swarm of nano sized biosensors that could record your EEG keystrokes.
Rootkit: A malicious piece of code is installed on IoT device that hides its identity to steal data, reconfigure the device, or control the system by executing malicious commands. This kind of attack is most dangerous as it bypasses all the security mechanisms and successfully hides its presence.
Now we're talkin! Something malicious is installed on an IoT device, meaning you, that steals your health by re-configuring your immune system function and thereby taking over your bodily systems and forcing them to execute malicious commands that disable you. Well, well, well… If that ain't just the perfect description of a vaccine bio-weapon I sure as hell don't know what is!
After all what is a booster shot if not the latest malware update, eh?
Countermeasures:
Access control, device hardening and system monitoring, Antivirus, Intrusion Detection. (See Section VI)."
Access control = "Your account has been suspended for violating TOC's"
Device hardening = "That’s all conspiracy theory"
System monitoring = "Don't read that without the proper context"
Antivirus = "Safe and effective"
Intrusion Detection = "That’s all mis/dis/mal information."
All these brave new medical advantages just keep sounding better and better, don't they? Don't be surprised if one day someone refers to the message below as "The Blue Screen of Health."
"Firmware updates are necessary in order to ensure proper device functioning. The firmware updates can be done remotely or directly(through usb port). An advertisement is usually broadcast on the network whenever a new version of the firmware update is available. Hackers can send false firmware update requests to the users in order to access the firmware and program it with malicious code. Fake firmware updates can cause fatal consequences to the patients.
Countermeasures:
Firmware Encryption, periodic firmware updates, malicious firmware detection."
C. SUMMARY ON THE SECURITY OF IOBNT
"The protection of IoBNT based systems is crucial as the consequences of security compromise can be detrimental. A summarization of existing security proposals for nanonetworks is presented in Table 6. Apart from the software attacks mentioned in the above section, there exist some other attributes can effect the security of IoBNT. The origin from where the attack has been instantiated can help in providing some insights into the profile and goals of the attacker. Local attacks require the attacker to be close to the physical location of the patient. Local attackers can replace the bio-electronics device with a maliciously programmed device, can eavesdrop the communication between bio-electronic devices and gateway devices to gather information to launch an active attack remotely. Remote attacks are launched outside the premises of the bio-electronic devices. These attacks can be launched by accessing the smartphone of the patient that is delegated a gateway device, to send malware and reconfiguration requests to reprogram the device. In wireless communication, attackers can evade the system in two possible ways: active and passive. Passive attack is launched by an attacker silently without revealing their presence in the system. A passive attack can violate the privacy of the patient and can reveal confidential information about the device.
By just intercepting the communication, a passive attacker can gather information like the patient’s location, diagnosed disease, type of treatment, etc. This information can be used to further mount active attacks. Active attacker not only enables the attacker to read the transmission but also uses this information to disrupt the communication. The active attacker can modify the messages in transit, drop the messages so they do not arrive at the destination, block the communication, reprogram the device and even induce a shock to the patient by manipulating the device. As the major application of area of IoBNT is bio medicine, therefore, breach in security means life threatening consequences."
Still think this is all impossible? Here is an example of the worst kind of hacking described in this paper already becoming a real problem.
PWNING ELECTROENCEPHALOGRAM (EEG) MEDICAL DEVICES BY DEFAULT
https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/pwning-electroencephalogram-eeg-medical-devices-by-default/
Key Takeaways:
Default credentials, while written off by the vendor in this case as seldom used and unnecessary to change, can lead to the exploitation of active directory environments.
The way NeuroWorks configures their EEG Software initially leads to a high likelihood of out-of-the box remote code execution.
If an administrator changes the default password, the software will not function properly, thus the vendor recommends not changing the default password.
Multiple host machines with the EEG software installed suffered from this vulnerability, allowing an emulated threat actor to obtain remote code execution on each host machine as a local user, and privilege escalate to obtain domain user credentials.
Depending on the environment, domain users who login to these machines could potentially have their credentials stolen, and with specifically assigned domain permissions – lead to a much larger compromise in the active directory network.
There’s a high probability of operating systems with Neuroworks Natus EEG Software installed lacking antivirus or endpoint detection response measures, making it a valuable target for threat actors to gain a foothold while trying to maintain network persistence.
Nobody is working all that hard to secure your biology.
The ability to able to maliciously hack your biology
was all this type of research has ever been about!
Next up in Part Seven:
VI. Potential Mitigation Strategies
HOW TO REVERSE VACCINE INJURIES:
http://estateartistry.com/blog/reversing-vaccine-injuries
CANCER CURE:
http://estateartistry.com/blog/cure-your-cancer-by-christmas

 RSS Feed
RSS Feed